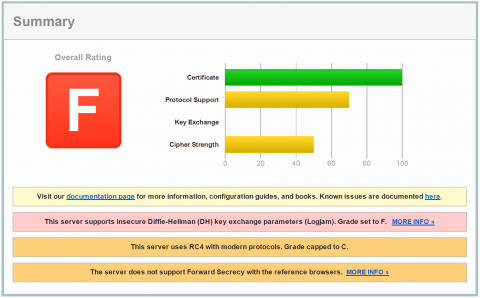
I just installed a Web Console on Windows 2012 R2 Core server and learned how insecure this system is out of the box. You may have worked through the Post-Installation Configurations for Web Server and Web Console. This ends with an highly insecure web server configuration. The SSL encryption is sooo weak that I tend to say you can also leave SSL switched off. You can check your server with SSL Server Test. Commvault default with Java 7 will end with the most worse test result of F.
Perfect Forward Secrecy
Last viewed:
- Setup Microsoft Windows or IIS for SSL Perfect Forward Secrecy and TLS 1.2
- ColdFusion 10: The CacheManager has been shut down. It can no longer be used
- ShoreTel: CallerID not shown on far end if call is redirected
- WiX: How to use RemoveFolderEx in your XML scripts
- Commvault: Enable Outlook Client Addon debugging